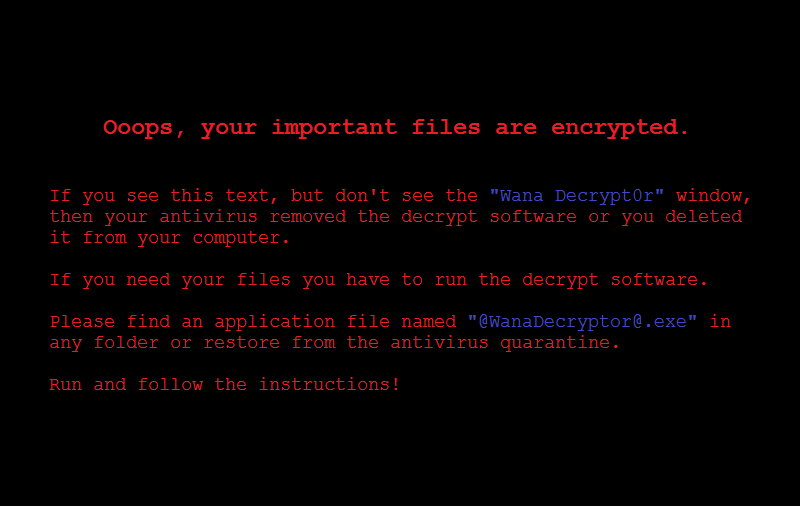
Residents should be aware that a massive ransomware attack has spread across the globe, locking up thousands of hospital, telecommunications, and utilities systems. The attack used data stolen from the NSA to exploit vulnerabilities in Microsoft Windows and deliver the WanaCrypt0r ransomware. The demand was for $300 per PC.
While the ransomware was first detected wreaking havoc in emergency rooms and doctors’ offices in the UK, the infection quickly spread worldwide, including to the US.
The public firestorm over the release and plague-like spread of WanaCryptOr late last week was still in full-throated roar when reports of variants of the ransomware being discovered began appearing.
The first updated version appeared two days after the initial attack and did not include any major revisions, but simply pointed to a new command-and-control website, which was quickly taken down. Cybersecurity researchers also found other versions of WanaCryptOr, or WannaCry, that did not require a C2 website and are still on the loose in the wild.
The latest figures have WanaCrypt0r infecting more than 200,000 computers in more than 100 countries, up from about 60,000 computers and 74 countries last week.
If you’re not currently using a malware/virus protection program from a vendor that guarantees to block this newest threat, I recommend that you update your Microsoft Windows software immediately. Microsoft released a patch for their vulnerability in March, but many users haven’t updated, leaving their computers open to this attack.
I just received an attempt to plant a ransomeware on my own desktop, through an email. The name it supposedly came from was one I recognized, but the senders email was not. Contained in the email was a message that simply said, “You have to see this.” A link was provided, which disguised an .exe (execute) file. My own paid program scanned the file and found it was ransomeware. I deleted the mail from my inbox and then from my trash folder.
Unless you are absolutely sure of the sender and the originating email address NEVER click attached links. You should also be wary of clicking links contained in emails that have been forwarded to you, even if you have verified the sender and his/her email. You can never be sure of who they received the email from.
Disclaimer: On January 4, 2016, the owner of WestEastonPA.com began serving on the West Easton Council following an election. Postings and all content found on this website are the opinions of Matthew A. Dees and may not necessarily represent the opinion of the governing body for The Borough of West Easton.