Borough computers fell victim to a Ransomeware this past week. Ransomeware infects computers by encrypting targeted files, then notifies the user that they must pay for a decryption key to get those files restored.
EZMicro, the company the borough hired to install and maintain the computer equipment was able to restore the server and computers without any major loss of data. “Backup copies of the office computers were reinstalled that resulted in only that day of work being lost,” said David Gehman, Senior Clerk for the Borough.
EZMicro reported the Ransomeware to be the one named, Teslacrypt. Tesla has a history spanning the last few years.
Although resembling CryptoLocker (the first such encryption ransomewares) in form and function, Teslacrypt shares no code with CryptoLocker and was developed independently. The ransomeware previously infected computers via the Angler Adobe Flash exploit.
Even though the ransomware claimed TeslaCrypt used asymmetric encryption, researchers from Cisco’s Talos Group found that symmetric encryption was used and developed a decryption tool for it. This “deficiency” was changed in version 2.0, rendering it impossible to decrypt files affected by TeslaCrypt-2.0.
By November 2015, security researchers from Kaspersky had been quietly circulating that there was a new weakness in version 2.0, but carefully keeping that knowledge away from the malware developer so that they could not fix the flaw. As of January 2016, a new version 3.0 was discovered that had fixed the flaw.
In May 2016, the developers of TeslaCrypt shut down the ransomware and released the master decryption key, thus bringing an end to the ransomware. After a few days, Kaspersky released a public tool to decrypt affected computers at no charge.
But the threat hasn’t ended. Other versions have been created that can no longer be removed using the simple decryption tool provided by Kaspersky.
One of those I got, before Borough Hall got theirs. Mine turned out to be CryptX, though it called itself, RSA4069 Key, an old version of Tesla.
If I’m ever thrown in jail it will be because I tracked down some low-life programmer and beat him to death with my laptop.
Unlike EZMicro, I don’t maintain backups of my entire computer in the “Cloud,” or on an independent server. This one took me 6 hours to solve and clean out of my computer.
The Crypt ransomeware encrypts photos, videos, and other files on your computer. In my case, some additional extensions that were hit were those ending in “.pdf” and “.html”. Some I spoke with on the Internet forums I belong to reported their Excel spreadsheet files were hit when they got infected.
Which is why I am going to begin deleting all the anti-Trump and anti-Clinton emails that I am getting deluged with lately and ask the senders to STOP including me in their mass mailings to everyone in their contact list.
Here’s what you will see on your screen, so you recognize it.
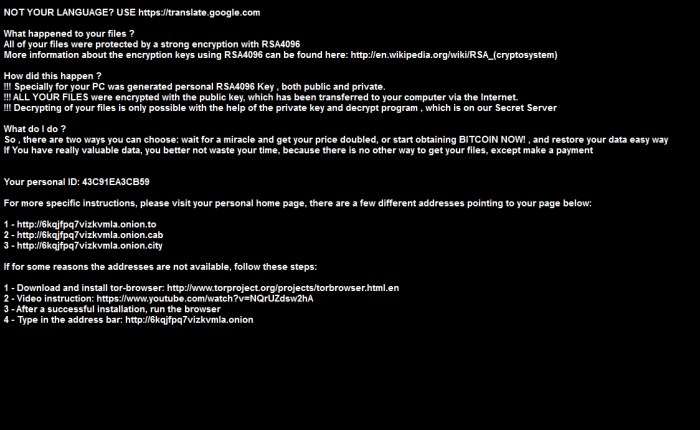 Your desktop screen goes to a black background and there is a message on your screen telling you your files have been encrypted with the RSA4096 Key. There is instructions on how to obtain the decryption program and a warning about how the price will increase ($500 if you pay immediately) if you wait. This is actually a picture that has replaced your background image.
Your desktop screen goes to a black background and there is a message on your screen telling you your files have been encrypted with the RSA4096 Key. There is instructions on how to obtain the decryption program and a warning about how the price will increase ($500 if you pay immediately) if you wait. This is actually a picture that has replaced your background image.
Pictures and other files on your computer will end with the extension “.de_crypt”. Your photos, for example, will display as, “photoname.jpg.de_crypt”. You won’t be able to open them with any program and renaming them by removing “,de_crypt” will not be successful. The ransomeware has already encrypted them.
Your computer will get popups with the same message in boxes. Your home page may be redirected to a landing page with the same message and a link provided to pay the ransome. Don’t pay the Bastards!
Luckily, unlike the FBI ransomeware I wrote about previously, just about all other functions of your computer aren’t affected. You can still surf the web, get mail, etc. Though, I did read that newer versions of this ransomeware are going full screen, preventing you from seeing the Start button and associated menu, similar to the FBI virus.
So, how can you fix this? You can do what I did, which is the long process that won’t cost you money, but I realize that most people won’t want, or even know how, to enter the registry files, among other areas of the computer.
So, I’ll give you an alternative that will cost you far less than the ransome and keep your computer safe from future malicious programs.
With both options (including my own manual removal), you need something very important to even have a chance at decrypting those files on your computer. You will need an ORIGINAL unencrypted file of a file that is encrypted on your computer. This means a file from a disk, thumb drive, or external hard drive that you will transfer back onto your computer. It can be a photo, a movie clip, or any other file. The bigger the file you have, the better, because the decryptor program will only decrypt files of the same size or smaller than the two “matched” files you use for it to decrypt your computer. Anything larger than your matched pair will remain encrypted, so try to find something over 1 megabyte in size.
The decryptor program can be found HERE. (Look for the link within the article that tells you it is available for downloading.)
I won’t go into detail about starting your computer in Safe Mode and entering Registry files to remove the actual infection coding. Any identifiers I would give you about .exe file names would likely be different from what you find, as there is no one, single file name with all the variations that are being created and sent out.
Your best bet, after decrypting your files, is to bring your infected computer to a reputable geek and have him remove the ransomeware coding.
After that, to prevent another infection, install Malwarebytes Anti-Malware. It Protects your from new online threats that antivirus can’t detect. The paid version, which I just switched over to (my free version didn’t provide “as-you-work” protection) detects intrusions and stops infections before they implant on your files.
Disclaimer: On January 4, 2016, the owner of WestEastonPA.com began serving on the West Easton Council following an election. Postings and all content found on this website are the opinions of Matthew A. Dees and may not necessarily represent the opinion of the governing body for The Borough of West Easton.







